
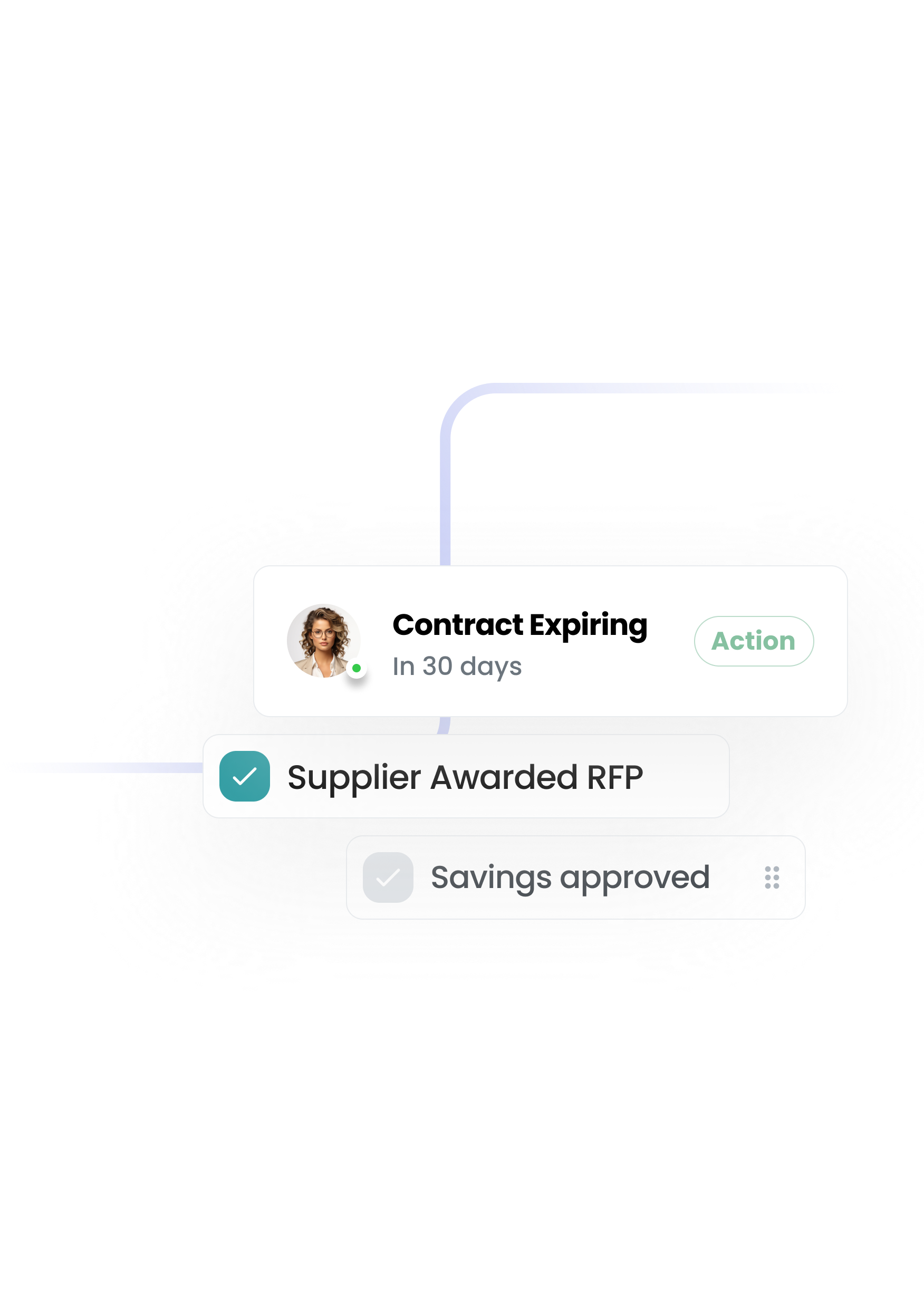
The first procurement system that configures to you — not the other way round. A platform that your team actually wants to use—built to remove the pain and give you control.



%20(3).png)
.png)

.png)















.png)

.png)









.png)

.png)
















.png)
.png)
"Other systems we've tried have felt so clunky and complicated that we haven't known where to start. Anyone looking to move away from the days of Excel should really consider trying this out."

"Very interactive, I can analyze supplier and manage all contracts within the platform. Really quick and easy to learn."

"Great price and really easy to use. Similar software's we tried only gave the basics and one other module for the same price however using oboloo I can manage my contracts, suppliers and create as many RFQ's as I like."

"Really user friendly, very powerful, feature rich, great to move away from excel spreadsheets."


Seamlessly connect oboloo with 1,000’s of other tools — no code required.
.png)
Tailor the platform to fit your linguistic preferences and streamline communication across your organization and with your suppliers.
Manual processes, scattered files, endless emails.

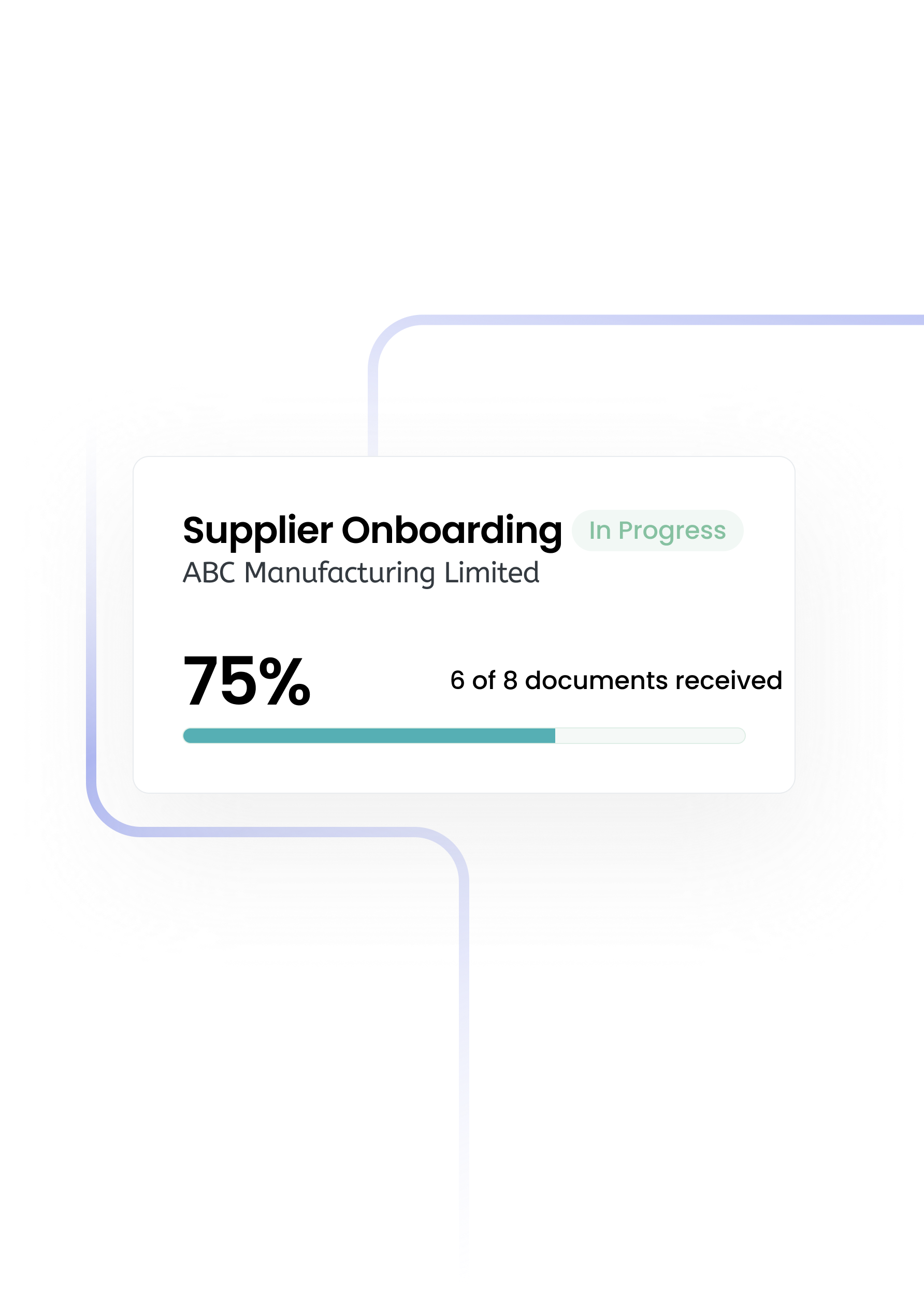
The single source of truth for procurement teams.

.png)
.png)
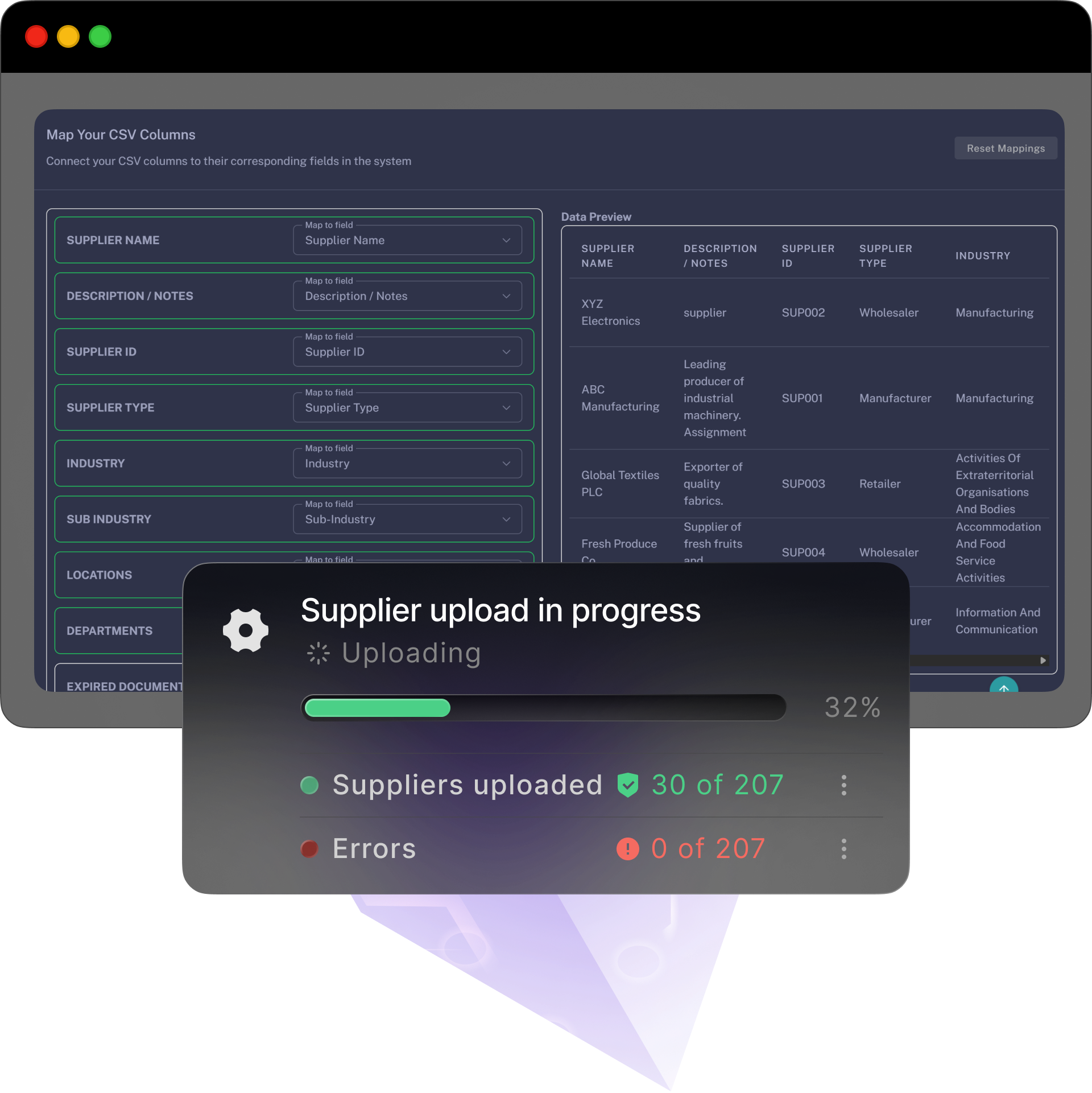
A simple, self-serve path with optional free and personlised onboarding and training — bring your data, follow the steps, and you’re live before the week’s out.
.png)

.png)




.png)